
The Fourth Industrial Revolution is upon us, with the digital transformation of business largely consisting of automation, AI, and rapid technological innovation. Industrial processes and machines are becoming smarter and more modular. A critical enabler of this transformation is the Internet of Things (IoT). Smart, always-connected devices provide real-time contextual information with low overhead to optimize processes and improve how companies and individuals interact, work, and live.
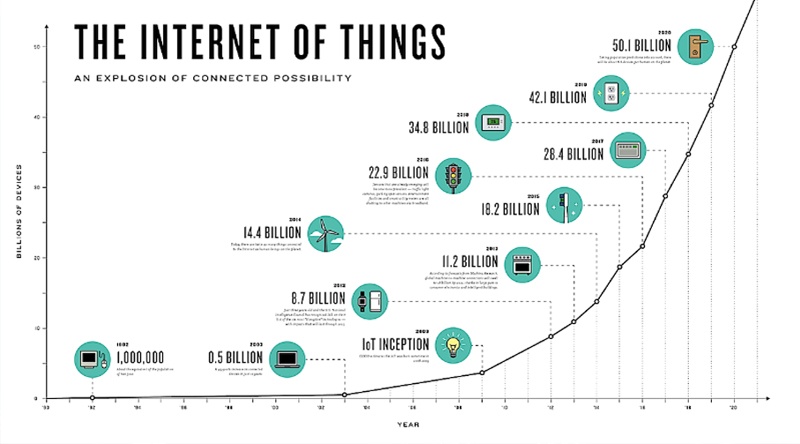
Over a million new IoT devices are connected to the Internet daily, and these numbers are accelerating. By the year 2020, experts predict there will be as many as 50 billion IP-enabled IoT devices. This growth in IoT is already contributing to an escalating explosion in data. When compared to traditional data center traffic, which will triple in the next three years to 15.3 zettabytes (ZB) according to Forbes, IoT growth over the same time is mindboggling—39 times higher or 600 ZB.
Emerging Threat of IoT
IoT transformation has not gone unnoticed by cybercriminals, who seek to exploit IoT as the weakest link in the data chain. The increasing volume of structured and unstructured data being generated by IoT devices, and their oftentimes anomalous behavior spanning across global ecosystems challenges even the best cybersecurity organizations. This past year, enterprises reported a 152 percent jump in IoT devices, and over a simultaneous three-month timeframe, a 130 percent jump in the number of reported IoT botnets. So it should come as no surprise that it is predicted that 25 percent of attacks on enterprises will target IoT devices within three years.
Not only are most cybersecurity organizations unprepared for the security threats posed by IoT, but so are cybersecurity providers. The ubiquitous interconnectivity between devices, users, and distributed networks presents a substantial challenge for traditional, silo-based security products. Defending a single point in the network is increasingly ineffective. Specifically, the lack of single view visibility across devices, users, and the entirety of the network creates blind spots that cybercriminals can exploit. According to a study conducted by EY, almost half of enterprises indicate they are concerned about their inability to track security across their IoT assets, keep them virus free, and patch vulnerabilities.
Chock Full of Risks
From a security perspective, IoT devices are chock full of risks. One problem is that most IoT devices were not designed with security in mind—many of them are headless (do not have a traditional operating system or even the memory or processing power required to include security or install a security client) while an alarming number have passwords hard-coded into their firmware. The result is that many IoT devices cannot be patched or updated. And even when security can be installed on the IoT device, the underlying installed software is often cobbled together from commonly available code or is untested, meaning that most installed security tools can be circumvented by exploiting a wide range of known vulnerabilities. Other security vulnerabilities include:
- Weak authentication and authorization protocols
- Insecure software
- Firmware with hard-coded backdoors
- Poorly designed connectivity and communications
- Limited to no configurability
Considering the above challenges, it isn’t surprising to find that 70 percent of the most commonly used IoT devices contain known security vulnerabilities. And when they are comprised, most IT organizations admit they are likely or highly unlikely to be able to detect the event before it impacts systems and data.
Things to Consider
Although some cybersecurity providers are beginning to address these issues by promoting authentication, key, and credential management, among other capabilities, these tools add to an already overly-complex security environment. In addition, these new capabilities need to be tested, integrated with the network architecture, updated, managed, and monitored—often stretching bandwidth and resource-constrained cybersecurity organizations beyond the breaking point.
So, what is the answer? Simply sticking your head in the sand will not work. IoT is a vital part of most businesses and is here to stay. The following are a few recommendations:
- Security must be redesigned to provide seamless visibility on what is happening across all networks and devices, from IoT to multi-cloud networks.
- Security monitoring and management needs to be done through a single console. Enterprises must be able to see all devices, access risk levels, segment traffic, and assign policies across the entire network in real time.
- Look for security solutions that automatically adapt to network changes, anticipate threats, interpret and implement business language commands, share threat intelligence, and proactively coordinate responses to threats across all security devices and network ecosystems.
- View IoT as part of your broader security environment rather than as isolated units.
Our white paper on “Understanding the IoT Explosion and Its Impact on Enterprise Security” provides more details on the security risks of IoT and what organizations can do to address them.






