As cloud-based services continue to increase in scope and scale, there isn’t a single organization that wouldn’t benefit in some way from the cloud. Indeed, with the promise of lowering OPEX, while reducing or even abolishing CAPEX, the cloud can enable an organization to better focus on its core business, which is something that every C level executive wants to hear these days.
As a result, the cloud has seen immense growth over the last couple of years. But the security risks that arise from such a profound change are not to be taken lightly.
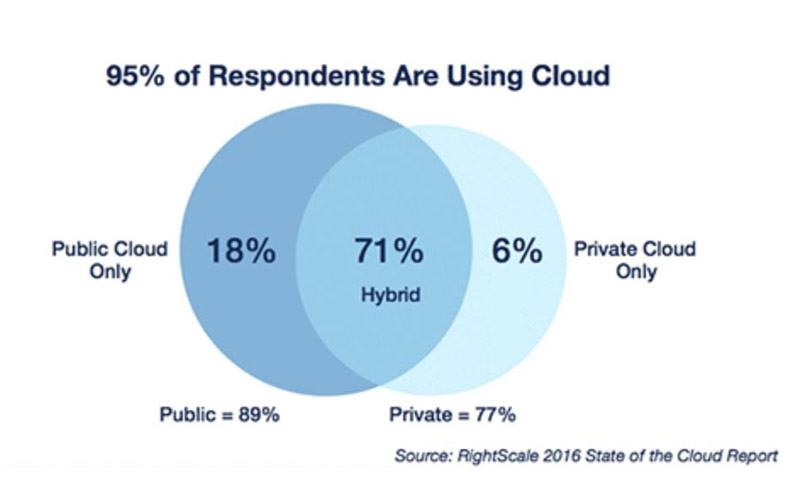
According to industry research, more than 95% of all enterprises today have at least one system on the cloud, with 71% of these companies having some of their assets running on a hybrid cloud. The cloud is here to stay, and has already shifted the way these companies conduct their business.
One of Fortinet’s predictions for 2017 is that the IoT will become the weakest link for attacking the cloud. That threat can come in many forms, as IoT devices have been shown to be more likely to contain easily exploitable vulnerabilities, making then a growing target for cybercriminals seeking, for example, to expand their botnets and weaponize them.
IoT-based DDoS attacks have already shown their power to disrupt business. The attack that recently hit the DYN infrastructure, for example, was so massive that it reached the 1Tb/s mark, with all traffic being sent from IoT devices.
Not only are IoT devices an attractive target because of their inherent insecurity, but also for the role they play in some organizations, such as CCTV Cameras, which can provide real time information about everything that is happening at a given location.
But vulnerabilties are not the only issue. As IoT devices are being deployed they must also be managed, and they are increasingly being managed by cloud solutions that require a communications channel between the IoT device and its master controller in the Cloud.
We expect to see attacks leverage this trust model in order to poison the cloud, and then use that beachhead to start to spread laterally. These end devices can then be exploited to misuse their trusted relationship to upload malware to, and distribute it from the cloud.
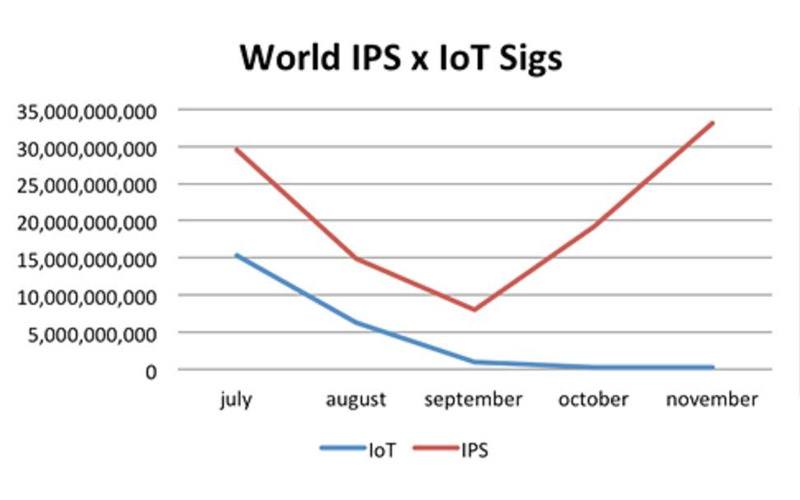
As we have seen from our global sensor network, attacks directed against IoT devices are growing exponentially and show no signs of stopping. They often come in waves, as shown in the above graphic, which shows an attack that targeted widely deployed routers last summer and fall. And since October, we have seen a rise in attempts to exploit the hardcoded backdoor vulnerability exposed on a wide array of CCTV-DVR products, yielding an exploit that can be used against a plethora of devices. We believe that the number of affected CCTV models is close to 80.
Another recent threat was the attempted expansion of the Mirai botnet that targeted German Telco broadband routers. In this case, however, rather than taking these devices over, a coding error in the malware made these routers crash, leading to a massive outage on the broadband services of this carrier.
Other than the coding error, this malware was very sophisticated, and included features to cleanse the infected routers of other infections such as Anime, Qbot, and LizardSquad Botnet.
Today, most cloud providers and IoT solutions lack the integrated security fabric, strict controls, and trusted authority necessary to provide ubiquitous security to this expanding business model.
But cloud poisoning and DDoS attacks are just the beginning. One of the most potentially damaging threats that can affect an IaaS service is a local privilege escalations exploit, like the Dirty Cow, where any user with access to a remote shell on a cloud server can leverage vulnerabilities to gain root level access on the VM box.
In this exploit, the vulnerability lies on the filesystem code on the Linux kernel. It enables a non-privileged user to write to any file on the system, enabling the attacker to do such things as inject code into the Linux kernel. Spotting such file modifications requires closely monitoring the integrity of crucial files.
Another potential risk lies in public cloud offerings where you may have business competitors sharing the same infrastructure. Fortinet security solutions address this challenge by enabling and securing the sort of microsegmentation required, preventing data leakage between these different cloud domains. This challenge can be addressed even when two competitors live on the same hypervisor. With the advent of the FortiGate VMX, it is possibile to provide deep inspection of traffic even when there is the need to search for threats that may exist in the communications between these two hosts.
Of course, the need for deep inspection coupled with low latency is where our FortiGate solution really shines. Our silicon-based SPUs (Security Processing Units) provide the horsepower needed to search deep into the packet, even if it is encrypted, and look for threats, with the lowest possible latency.
Securing the cloud requires adequately protecting it from the vulnerabilities being introduced by IoT devices that are not designed with adequate security. Access control, distributed threat intelligence, and consistent security that can span across physical and cloud environments is essential to safeguard against today’s cloud-based risks. Fortinet security solutions, woven together through the Fortinet Security Fabric framework, enable organizations to embrace the power of the cloud with confidence.






